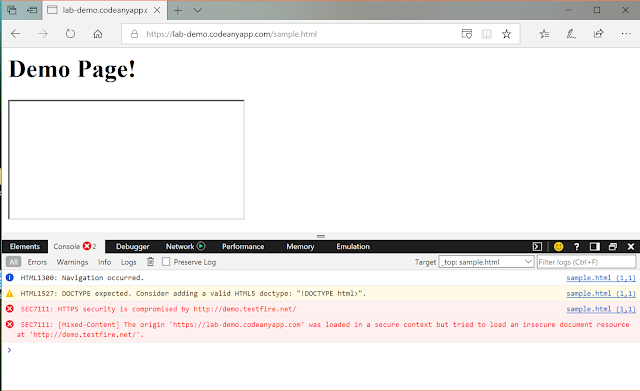
Hello readers, This post is about an edge mixed content security policy bypass. What is mixed content issue? According to MDN resource when a user visits a page served over HTTPS, their connection with the web server is encrypted with TLS and is therefore safeguarded from most sniffers and man-in-the-middle attacks. An HTTPS page that includes content fetched using clear text HTTP is called a mixed content page. Pages like this are only partially encrypted, leaving the unencrypted content accessible to sniffers and man-in-the-middle attackers. That leaves the pages unsafe. In short if we request to load any HTTP resources like scripts, stylesheets, video etc. over HTTPS then browser simply deny the request. Since HTTP resources can be intercepted by the attacker. For example suppose we have a page over HTTPS let’s call it https://securepage.com/secure.html Now request to create an iframe inside it to load an insecure resource http://demo.testfire.net and see how edge r