Lord of the root CTF walkthrough
Hi Guys, today we will walkthrough the Lord of the root CTF challenge. You can find this interesting challenge Here. As stated by the author our goal is to root the box and find out the flag.txt file so let's start ;)
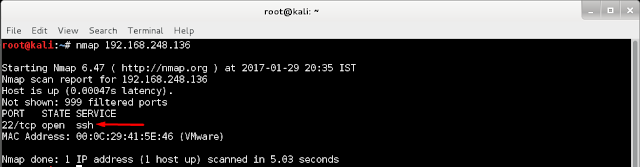
As always our first task is to do strong enumeration so let's start with nmap to check for different services and ports running on target machine.
Nmap shows only port 22 is open let's access it and see if we get any hint to move further.
Basically it gives us the hint for port knocking on port 1,2,3. There are many ways for port knocking but we will use following simple shell script.
Let's run this script for our target IP and ports.
After that let's again run nmap and check for open ports.
As a result of port knocking we got another open port i.e port 1337.
Sounds good ? let's access it.
So now let's run nikto to get some juicy information about the target.
But unfortunately nikto shows nothing important. Next i checked the source code for further hint but didn't get anything so after that i decided to run dirbuster to extract some directories.
As a result of dirbuster i got some directories among them icons sounds interesting.
Next i checked the source code and found a interesting hash code.
hash looks like base64 let's decode it ;).
After decoding it once it says "Closer !" so i decoded rest of code again and got a file named /978345210/index.php. Let's access it ;)
Wooh ! we reached to the gates of Mordor next i tried many ways to bypass it but didn't succeed and at last i started playing with SQLMAP. After digging around i found that its actually vulnerable to time base SQL injection.
So let's fetch database
Next i extracted Webapp database and found the following tables.
Let's look inside the users tables ;)
finally we get the username and password columns so let's extract one by one.
- Username column dump
- Password column dump
After that i logged in and found nothing to move further but as of now we have all the login credentials so let's access ssh port using smeagol's account.
So now we are logged in as smeagol next our task is to do Privilege Escalation. Let's do some enumeration again.
- Os Release
Since the target machine is running on ubuntu 14.04 with kernel version 3.19.0-25, the first thing we can try very popular exploit called overlayfs
which suppose to work for it.
Let's download and run the exploit.
Awesome we got the root access so let's goto root directory and access the Flag.txt file.
Thanks for reading.




















Comments
Post a Comment