Story of a JSON XSS
Hi folks,
This
post is about of one of my recent my finding in a bug bounty program. I started
checking the application for common vulnerabilities but got nothing after
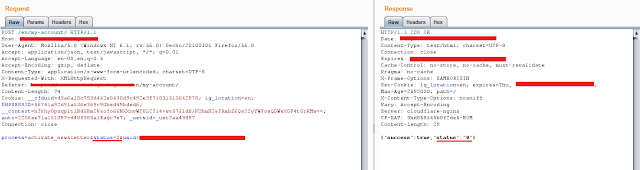
spending an hour I came across an endpoint which looks as follows.
If
you look at request and response you will see the value of status parameter is
reflecting back in the response. So I tried replacing the value of status
parameter and same reflected back in the response as shown in below.
What
next? Let’s check for XSS with a simple payload as shown in below.
But
angle brackets getting filtered, after I tried some encodings but nothing
worked. So I was about to give up but suddenly i decided to try array
tricks.
So
you can see whatever we write inside the round brackets is reflecting back in
response as it becomes associated array as follows
Status
Equals JSON object
<haha>
Equals
Key of JSON object
Test
Equals value JSON object
Let’s
check again for XSS with a simple payload
So
now angle brackets working for us but what if we apply = here
This
will break the query and that is why we are getting null value. Next I tried
URL encoding which worked for me as shown in below figure
Now
we are all set to make the final payload.
And
finally we need a CSRF POC in order to exploit it.
But the userid parameter was impossible to guess although i checked other end-points as well to get userid but don't get success and reported this vulnerability, they fixed it quickly because the entire website was using the same concept to display JSON data. And at last rewarded with decent bounty ;)
Thanks for reading









Great find and great write-up!!! More to come from you!
ReplyDeleteThanks mate, Sure i will write more ASAP :)
Deletegreat bro
ReplyDeletewhat if any of the parameter does not got reflected in response? Is is still possible to inject? I've tried to inject a new parameter, tried to inject into the parameter but nothing went good for me :/ any suggestion?
ReplyDeleteAlso another issue here is the content type in response is set to text/html which should be set to json
ReplyDeleteDo you think if Content-Type would have been "Application/json", then it would have been executed on browser? Asking this because I just tried this in one of the applications and it is reflecting in response but Content-Type is Application/json.
ReplyDeleteGood Post, I agree with Suraj if the content type in the response shows Application/json then we cannot do anything. I see here the response was in text/html.
ReplyDeleteSuperb post man..Thanks for contributing to community..cheers..!!!
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDelete